Science
Researchers Expose Satellite Data Vulnerabilities with Low-Cost Gear

A team of researchers from the University of Maryland and the University of California, San Diego has revealed significant vulnerabilities in satellite communications. Using basic electronics costing less than $600, the researchers successfully intercepted unencrypted data transmitted via global satellite networks. Their findings raise urgent concerns about the security of both military and commercial satellite infrastructure.
The study highlights that the risks associated with satellite data interception extend far beyond high-value targets traditionally associated with such threats. With the advent of accessible technology, individuals with modest technical knowledge can now tap into sensitive communications, challenging existing assumptions about cybersecurity. Previous analyses suggested that only government agencies or large organizations had the capability to exploit these channels. This new research demonstrates that even commercially available hardware enables monitoring of substantial data flows.
Research Methodology and Findings
Over a period of seven months, the researchers scanned signals from 39 geostationary satellites across 25 locations, examining a total of 411 Ku-Band transponders. These transponders are commonly used for television and internet connectivity, particularly in remote and rural regions. Much of the data intercepted included communications from both commercial and governmental networks, which were transmitted without any encryption or basic scrambling.
The analysis revealed a range of unencrypted transmissions. For instance, the team intercepted SMS messages, call content, and internet browsing data from T-Mobile users, as well as similar leaks from other providers such as TelMex, WiBo, and KPU Telecommunications. Notably, military communications from sea vessels were also captured, providing insights into ship names and internal management data. The researchers’ equipment passively intercepted these signals as part of backhaul and remote connectivity services.
Response to Security Vulnerabilities
Following their findings, the researchers notified several organizations, including T-Mobile, AT&T, IntelSat, and Panasonic Avionics. They declined requests to keep their findings confidential and engaged in discussions with representatives from the U.S. military and the Mexican government. The study underscored a widespread lack of consistent security monitoring or encryption practices for satellite-relayed traffic.
In their statement, the researchers noted, “Many organizations appear to treat satellites as any other internal link in their private networks.” They emphasized the accessibility of these vulnerabilities, asserting that “any individual with a clear view of the sky and $600 can set up their own GEO interception station from Earth.” This starkly contrasts with the expectation that sensitive commercial and governmental traffic would employ standardized encryption to prevent eavesdropping.
As reliance on satellite infrastructure continues to grow, especially for critical services, the study calls for a reevaluation of security measures. The absence of rigorous protection and the underestimation of interception practicality are concerning, as many entities still lack adequate safeguards against passive interception.
The research advocates for the implementation of robust encryption as a standard practice across satellite communications. Without proper measures, information transmitted via these channels remains at risk of exposure to relatively uncomplicated interception methods. Standard encryption protocols, such as IPSec, are not universally enforced, which allows plaintext data to traverse essential domestic and international routes without adequate protection.
In conclusion, as the dependence on geostationary satellites increases, particularly in military, commercial, and public applications, prioritizing effective encryption measures is crucial. Focusing on encrypted-by-default systems and conducting regular security audits can significantly mitigate risks posed by inexpensive and easily configured satellite interception hardware, thereby safeguarding both corporate and individual privacy on a global scale.
-

 Health3 months ago
Health3 months agoNeurologist Warns Excessive Use of Supplements Can Harm Brain
-

 Health3 months ago
Health3 months agoFiona Phillips’ Husband Shares Heartfelt Update on Her Alzheimer’s Journey
-

 Science2 months ago
Science2 months agoBrian Cox Addresses Claims of Alien Probe in 3I/ATLAS Discovery
-

 Science2 months ago
Science2 months agoNASA Investigates Unusual Comet 3I/ATLAS; New Findings Emerge
-

 Science1 month ago
Science1 month agoScientists Examine 3I/ATLAS: Alien Artifact or Cosmic Oddity?
-

 Entertainment5 months ago
Entertainment5 months agoKerry Katona Discusses Future Baby Plans and Brian McFadden’s Wedding
-
 Science1 month ago
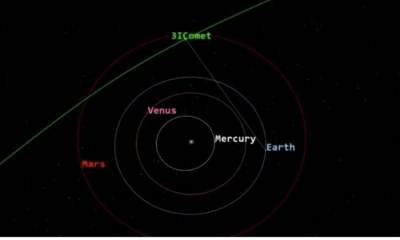
Science1 month agoNASA Investigates Speedy Object 3I/ATLAS, Sparking Speculation
-

 Entertainment4 months ago
Entertainment4 months agoEmmerdale Faces Tension as Dylan and April’s Lives Hang in the Balance
-

 World3 months ago
World3 months agoCole Palmer’s Cryptic Message to Kobbie Mainoo Following Loan Talks
-
 Science1 month ago
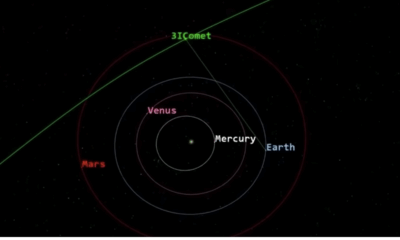
Science1 month agoNASA Scientists Explore Origins of 3I/ATLAS, a Fast-Moving Visitor
-

 Entertainment2 months ago
Entertainment2 months agoLewis Cope Addresses Accusations of Dance Training Advantage
-

 Entertainment3 months ago
Entertainment3 months agoMajor Cast Changes at Coronation Street: Exits and Returns in 2025