Business
Encryption Key Management: Securing AI Data in a Digital Age

The rapid evolution of encryption key management has become vital for safeguarding sensitive data within the AI industry. As organizations increasingly rely on AI models that process vast amounts of confidential information, the security of encryption keys has shifted from a back-end function to a critical component of data protection. In essence, effective encryption key management ensures that sensitive data remains secure as it traverses various environments.
What is Encryption Key Management?
Encryption key management refers to the systematic process of creating, storing, and rotating the keys that protect encrypted data. It serves as the control center for all encryption-related activities, determining who has access to the keys, when they expire, and how they are utilized. Without comprehensive management, even the strongest encryption can be compromised. A single exposed key can grant attackers unrestricted access to sensitive data. Key management systems mitigate this risk by securely storing keys, automating their rotation, and ensuring that only authorized users can access them. In AI environments, where data flows continuously between different systems, robust encryption key management is now essential for maintaining security.
The Importance of Strong Key Management for AI Models
AI models thrive on extensive datasets, which often contain sensitive information that must be protected at all times. Without effective encryption key management, the risk of exposing encrypted data increases significantly if keys are misplaced or improperly reused. The complexity of AI ecosystems, which often involve data lakes, APIs, and multi-cloud pipelines, makes manual key management untenable. Centralized key management solutions automate this process, ensuring timely key rotation while providing transparency regarding key access. Solutions like Akeyless Encryption Key Management offer a unified platform to manage all encryption keys securely across both cloud and on-premises environments.
Key Features of an Effective Encryption Key Management System
A well-designed encryption key management system can significantly enhance an organization’s security posture. Here are essential features to consider:
– A centralized, encrypted vault for all keys, promoting control and monitoring.
– Regular key changes to prevent long-term exposure and unauthorized access.
– Role-based access control, reducing the risk of misuse.
– Comprehensive tracking of key access for compliance purposes.
– Compatibility with various cloud providers, which is vital for hybrid AI setups.
– Simplified encryption and decryption processes within applications without exposing keys.
– Adherence to standards such as GDPR and HIPAA to maintain data integrity.
– Scalability to accommodate growing data and workloads.
Implementing Encryption Key Management
Once an organization identifies the necessary features for its encryption key management system, the next step is implementation. There are three primary approaches organizations can take:
1. **In-House Management**: This provides full control but demands significant expertise, time, and financial resources. It is generally suitable for large enterprises with dedicated security teams.
2. **Integrated Solutions**: While convenient and well-suited for specific environments, these solutions often lack flexibility in hybrid or multi-cloud contexts.
3. **Enterprise Solutions**: Many organizations find that enterprise-grade tools offer the most efficient balance between control and ease of use. These solutions provide automation, policy enforcement, and centralized management without imposing excessive overhead.
Conclusion
As AI models become increasingly data-driven, the importance of robust encryption key management cannot be overstated. This system is pivotal in ensuring that sensitive information remains private, traceable, and secure throughout its lifecycle. The growing reliance on encryption key management underscores its transition from a secondary function to a fundamental aspect of AI and data strategies. Solutions like Akeyless facilitate this process by automating encryption control, streamlining compliance, and enhancing trust in AI systems. For organizations building or scaling AI models, effective encryption key management is not merely an option; it has become an indispensable necessity.
-

 Health3 months ago
Health3 months agoNeurologist Warns Excessive Use of Supplements Can Harm Brain
-

 Health3 months ago
Health3 months agoFiona Phillips’ Husband Shares Heartfelt Update on Her Alzheimer’s Journey
-

 Science1 month ago
Science1 month agoBrian Cox Addresses Claims of Alien Probe in 3I/ATLAS Discovery
-

 Science1 month ago
Science1 month agoNASA Investigates Unusual Comet 3I/ATLAS; New Findings Emerge
-

 Science4 weeks ago
Science4 weeks agoScientists Examine 3I/ATLAS: Alien Artifact or Cosmic Oddity?
-
 Science4 weeks ago
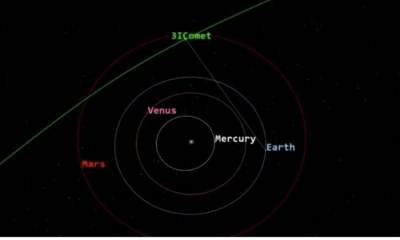
Science4 weeks agoNASA Investigates Speedy Object 3I/ATLAS, Sparking Speculation
-

 Entertainment4 months ago
Entertainment4 months agoKerry Katona Discusses Future Baby Plans and Brian McFadden’s Wedding
-

 Entertainment4 months ago
Entertainment4 months agoEmmerdale Faces Tension as Dylan and April’s Lives Hang in the Balance
-

 World3 months ago
World3 months agoCole Palmer’s Cryptic Message to Kobbie Mainoo Following Loan Talks
-
 Science4 weeks ago
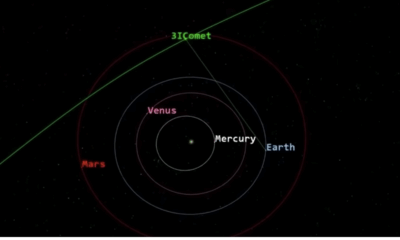
Science4 weeks agoNASA Scientists Explore Origins of 3I/ATLAS, a Fast-Moving Visitor
-

 Entertainment4 months ago
Entertainment4 months agoLove Island Star Toni Laite’s Mother Expresses Disappointment Over Coupling Decision
-

 Entertainment3 months ago
Entertainment3 months agoMajor Cast Changes at Coronation Street: Exits and Returns in 2025









