Business
5 Essential Steps to Strengthen Supply Chain Security Now

Retailers are increasingly vulnerable to cyber threats, as highlighted by recent breaches affecting major brands like the Co-op, Harrods, and M&S. The latter estimates losses of approximately £300 million due to a ransomware attack that exposed weaknesses in their supply chain. As cybercriminals become more adept at exploiting vulnerabilities, businesses must take proactive measures to enhance their supply chain security.
To build a resilient supply chain, organizations can implement five key strategies aimed at safeguarding operations against external threats. These steps focus on mitigating risks associated with third-party vendors, mapping supply chains, reinforcing API security, adopting a Zero Trust Architecture (ZTA), and preparing for potential incidents.
Mitigation of Third-Party Risks
One of the most significant challenges retailers face is ensuring their partners adhere to stringent cybersecurity standards. A common misconception is that the shared-responsibility model absolves retailers from accountability in the event of a third-party breach. In reality, it is crucial for retailers to conduct rigorous vendor risk assessments before entering contracts. This process involves evaluating potential partners based on their cybersecurity practices and ensuring compliance with regulatory guidelines.
Vetting vendors is an essential first step. Retailers should insist on receiving copies of the latest security audits and engage vendors in security questionnaires. This proactive approach helps ensure that all partners maintain consistent cybersecurity standards, ultimately protecting the supply chain.
Mapping and Securing the Supply Chain
A comprehensive understanding of the supply chain is vital for effective security measures. Retailers should create detailed maps of their supply chain operations, accounting for every supplier, manufacturer, and distributor involved. This blueprint helps identify potential vulnerabilities that could be exploited by cybercriminals.
As supply chains often include numerous third-party systems, it is important to standardize data exchange protocols. This standardization ensures secure data flows across various touchpoints, significantly reducing the risk of data breaches. Given that millions of APIs are in use, many of which are publicly accessible, security must be reinforced at a granular level. Implementing robust authentication and authorization policies is essential to prevent unauthorized access to applications.
The introduction of rate limits can also protect applications from becoming overwhelmed by excessive requests, ensuring consistent service availability. By establishing these security measures, retailers can create a strong barrier to protect both data at rest and data in transit.
Adopting a Zero Trust Architecture
Implementing a Zero Trust Architecture can further enhance supply chain security by ensuring that no connection is trusted by default. This model operates on the principle of “never trust, always verify,” requiring stringent verification processes for all users, even those within the network perimeter. Multi-factor authentication (MFA) and biometric validation are critical components of this approach.
Zero Trust Architecture streamlines security by segmenting the network and applying a “least privilege access” principle. This strategy ensures that only authorized users have access to sensitive resources, reducing the risk of systems being compromised.
As network complexity poses significant challenges for IT professionals, maintaining transparency is vital. Retailers can employ Secure Access Service Edge (SASE) solutions to combine networking and security capabilities into a single cloud-native service. This approach provides complete visibility over the network, enabling comprehensive supply chain security.
Preparing for Cyber Incidents
Despite the best efforts at prevention, breaches may still occur. Retailers must be ready to respond effectively to cyberattacks with a well-defined Cyber Incident Response Plan (CIRP). This plan should categorize risks based on severity levels and clearly delineate roles and responsibilities across the supply chain.
A comprehensive CIRP not only guides IT professionals in neutralizing threats swiftly but also includes processes for root cause analysis and thorough post-mortem investigations. These steps are crucial for patching vulnerabilities and preventing future occurrences.
The retail sector is currently facing unprecedented exposure to cybercrime, driven by increasingly sophisticated tactics employed by cybercriminals. By adopting proactive supply chain security measures, retailers can minimize their risk of breaches and safeguard their operations.
In conclusion, the dynamic nature of cyber threats requires retailers to be adaptable. By implementing these five essential steps, organizations can fortify their supply chains against cyber risks, ensuring that they remain resilient in a rapidly evolving digital landscape.
-

 Health3 months ago
Health3 months agoNeurologist Warns Excessive Use of Supplements Can Harm Brain
-

 Health3 months ago
Health3 months agoFiona Phillips’ Husband Shares Heartfelt Update on Her Alzheimer’s Journey
-

 Science1 month ago
Science1 month agoBrian Cox Addresses Claims of Alien Probe in 3I/ATLAS Discovery
-

 Science1 month ago
Science1 month agoNASA Investigates Unusual Comet 3I/ATLAS; New Findings Emerge
-

 Science4 weeks ago
Science4 weeks agoScientists Examine 3I/ATLAS: Alien Artifact or Cosmic Oddity?
-

 Entertainment4 months ago
Entertainment4 months agoKerry Katona Discusses Future Baby Plans and Brian McFadden’s Wedding
-
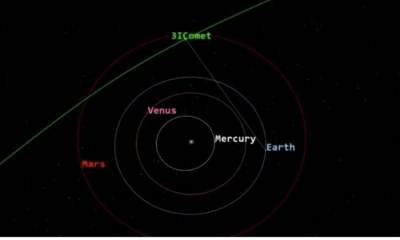
 Science4 weeks ago
Science4 weeks agoNASA Investigates Speedy Object 3I/ATLAS, Sparking Speculation
-

 Entertainment4 months ago
Entertainment4 months agoEmmerdale Faces Tension as Dylan and April’s Lives Hang in the Balance
-

 World3 months ago
World3 months agoCole Palmer’s Cryptic Message to Kobbie Mainoo Following Loan Talks
-
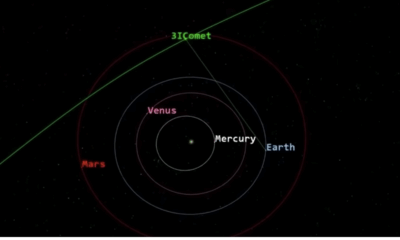
 Science4 weeks ago
Science4 weeks agoNASA Scientists Explore Origins of 3I/ATLAS, a Fast-Moving Visitor
-

 Entertainment4 months ago
Entertainment4 months agoLove Island Star Toni Laite’s Mother Expresses Disappointment Over Coupling Decision
-

 Entertainment3 months ago
Entertainment3 months agoMajor Cast Changes at Coronation Street: Exits and Returns in 2025









